Don't Neglect Your Network's Weakest Link: Securing Your Layer 2 with DrayTek
The Threat
Despite having an advanced firewall protecting your network from the Internet your network might still be vulnerable to LAN-originated attacks.
Layer 7 and Deep Packet Inspection Firewalls are gaining in popularity. The promise is that sophisticated algorithms and usually high price-tag equipment and licenses can protect your network from all the dangers found online. This function is, in most cases, performed by the firewall that resides between your LAN and the Internet. Smart Layer 7 Firewalls and behavior detection continues to develop but neglects the Layer2.
In this category it has been difficult to find the right product for SMBs, until now. DrayTek security routers are an excellent choice as they offer a tremendous value for SMBs - including most of the security features provided by mainstream firewalls at just a fraction of the price.
The Biggest Security Threat May Be Inside Your Network
However, most firewalls suitable for SMBs cannot combat Layer2 attacks because they happen at the LAN level before traffic reaches the firewall. Many times it is forgotten that the most dangerous threat comes from inside the LAN and little effort is made to protect it. Anyone managing a LAN - including IT professionals, Integrators, and MSPs - need to have better control. IP cameras, printers, IP phones and many IoT devices are connected to networks everyday and they are becoming the biggest threats as some of them, usually cheap, can contain malicious code or are easily hackable. Several cases were raised by the media recently about hundreds of thousands of printers, cameras, and routers compromised and running malicious code. All of those devices are in the LAN and can target PCs and other devices within the LAN.
Malicious or mistakenly duplicated IPs, rogue connections, infected hosts, ARP spoofing, ARP poisoning, etc., can bring your network down no matter how advanced your Internet facing firewall is. A network loop created when someone connected a network cord to the wrong place is also a common problem that disrupts the network. All happens at the Layer2 and can be prevented in the network switch.
It’s not difficult to connect a device to an existing network and completely mess it up! Any active open network port or switch, the wall, or the back of an IP phone will allow for a new device to access your network. Connecting a small switch to a working network port in the building can open physical access of your LAN to rogue devices.
Finding out the IP address subnet of a network is easy to do by just looking at the IPs assigned by the DHCP server. A rogue device can be connected to the network with a statically configured duplicated IP of key elements of the network such as the router, DNS, PBX (if local), print and file servers, etc. Infected legitimate hosts can have the same effect on the network without any physical intervention.
The result is that the network starts becoming erratic and slow. When something like this happens it can take days for an experienced network technician to diagnose and resolve the issue. Hours of network captures and comparing MAC addresses to find leads in hundreds of thousands of packets can be overwhelming.
Again, all of this happens at the Layer2 and can be prevented in the network switch.
The Solution
Fortunately all of the above described nightmares can be avoided inexpensively if using the right network switches and configuring them accordingly. There are Intrusion Detection Systems (IDS) on the market that can help mitigate this threat but there is not one suitable for SMBs that are not complicated and do not break the bank.
Many business switches on the market can help with preventing network loops, segmenting networks with VLANs or defining ACLs to fixing MAC addresses to port to prevent some of the threats described previously. The problem is that those network switches are not only complicated or expensive but also most do not offer the extra intelligence needed. A new breed of security switch would need to act as a Layer2 Firewall. The switch is the entry point for any Layer2 connection and is the natural place to implement such features.
DrayTek’s business switches, the 1280, 2280x, 2121 and 2500 families, released a set of features this year that enhanced the built-in security tools available to and needed by IT and networking professionals, integrators, and MSPs. With DrayTek, there is no need for maintenance contracts and firmware upgrades are always available at no cost. Some of the new features to countermeasure the LAN threats are:
Simple Layer2 Port Security
This feature protects your network from unauthorized or rogue connections by specifying the type of Layer2 host allowed in your network. Simple configuration through a wizard or GUI makes it easy to setup your Layer2 network securely without having to deeply understand Layer2 Firewalls. Few options can be configured and changed by just clicking at the port:
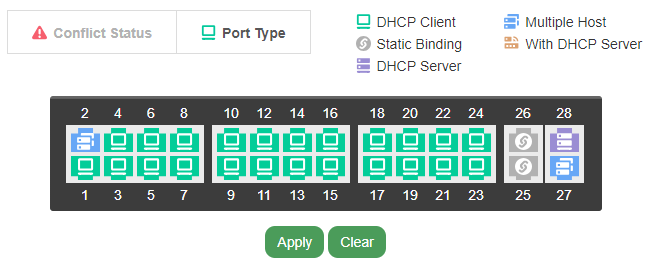
DHCP Client or Static
You can define what ports can accept statically-configured IPs or DHCP clients disallowing intruders trying to configure the clients differently and connecting to the network.
Multiple or Single host port
You can also set a port to accept only one device or multiple devices. With this you are protected against rogue switches running multiple hosts connected to the other end of the wire. You define what is allowed - up/downlink ports that can run multiple MACs.
Unique IP-port binding
Server ports can be statically bound to ports. The switch won’t allow any other port running a host with the same IP preventing malicious or mistakenly configured duplicated IPs that can greatly disrupt the service.
DHCP Server port
Prevent rogue or duplicated DHCP servers in your network. Malicious code can make any host become a DHCP server for your network redirecting traffic to itself and relaying it with the purpose of sniffing the traffic while going unnoticed. Misconfigured IP phones, cameras, or routers can also act as a DHCP server.
IP Source Guard
This enables the network administrator to specify the IP or IP-MAC allowed to connect to the network on any specific port. This binding helps prevent rogue connections to specific ports in the switch. You can lock ports to only work with legitimate devices connected.
In the example below, anything connected to port 24 or 25 that is not the specified server’s MAC and IP will be blocked.
Layer2 Firewall for MAC, IPv4 and IPv6.
This is the more full feature Layer2 built in Layer2 Firewall for added flexibility creating the rules for MACs and IP addresses. You can protect critical servers from being accessed and even shut down the offending source. Rules are then bound to all or specific subsets of ports.
Below is an example of rules to restrict access at the MAC level. None of these connections would be seen by a traditional firewall.
The example rule below restricts access to the printers in the company. It will protect the printer from being targeted on different ports and if it receives malicious code it can prevent it from connecting to other hosts. All of the IP connections in the same subnet do not pass through the router or traditional firewall.
Stay tuned for future BLOGS and learn how the information gathered by the Layer 2 switches can be captured and analyzed by DrayTek's ACS and by the IPTECHVIEW platform for managing and monitoring IP Technology Devices.







